Privacy rules – Fessing up when things go wrong
The Notifiable Data Breaches (NDB) scheme under the Privacy Act was introduced to protect individuals.
Effective on 22 February 2018, it is mandatory for organisations complying with the Act to report significant data breaches to the Office of the Australian Information Commissioner (OAIC) and the affected individuals. This is not a new concept as it currently operates voluntarily under the Act. Previously, reporting data breaches was only voluntary.
The new NDB scheme introduces compulsory disclosure for organisations with annual turnover of $3M and above and entities who meet the various “test categories” listed below.
A Notifiable Data Breach could occur when a customer’s or employee’s personal information on a device (e.g. USB key) is lost or stolen, a database is hacked or personal information is mistakenly provided to the wrong person or made public.
Personal information – defined
Personal information (including sensitive information) is information or an opinion that identifies or could reasonably identify an individual. Generally this includes: name, address, telephone number, signatures, date of birth, medical records, bank account details, etc. It also includes opinions about someone including comment on a person’s career, performance, attitudes and aptitude.
Sensitive information is a subset of personal information and is generally afforded a higher level of privacy protection under the scheme. This includes racial or ethnicity origins, political, sexual orientation, philosophical beliefs, health information, criminal records etc.
Reporting serious harm
To avoid creating “data breach fatigue”, the OAIC only requires data breaches “that are likely to cause serious harm to individuals” to be reported. Serious harm means the breach is more probable than not likely to cause psychological, emotional, physical, and reputational harm to individuals.
The Act requires an assessment by the organisation from a reasonable person’s perspective to determine the likely serious harm based on the following:
![]() The type of personal information involved (i.e. ubiquitous, sensitive, confidential, or financials)
The type of personal information involved (i.e. ubiquitous, sensitive, confidential, or financials)
![]() Who is affected by the breach
Who is affected by the breach
![]() What remedial actions have been taken or what security measures were in place (i.e. encryption etc.)
What remedial actions have been taken or what security measures were in place (i.e. encryption etc.)
![]() What parties have gained unauthorised access to the personal information.
What parties have gained unauthorised access to the personal information.
Who will be affected?
The NDB scheme applies to both the private and public (commonwealth agencies only) sectors. It can apply to individuals (including a sole trader), body corporates, partnerships, unincorporated associations and trusts.
Test categories
Generally, if an entity’s annual turnover is $3 million and above, it is bound by the NDB Scheme. However, smaller businesses may still need to comply due to their need to handle personal information and the nature of their operations including:
![]() Commonwealth contracted service providers
Commonwealth contracted service providers
![]() TFN recipients (lawyers, accountants, tax agents etc.)
TFN recipients (lawyers, accountants, tax agents etc.)
![]() Credit reporting agencies
Credit reporting agencies
![]() Traders in personal information
Traders in personal information
![]() Health service providers
Health service providers
![]() Related parties or contractors of an entity bound by the scheme
Related parties or contractors of an entity bound by the scheme
![]() Operators of a residential tenancy database
Operators of a residential tenancy database
Other regulations
Entities could also be prescribed by the Privacy Regulation 2013, or bound by the scheme by other regulations.
Self-opted
If none of the above applies, the scheme will apply to entities that choose to participate in the scheme as best practice.
Implementation in your organisation
The aim of the scheme is to ensure that ongoing reasonable steps are performed to protect personal information (including sensitive information) from misuse, interference and loss, as well as unauthorised access, modification or disclosure.
This is an objective test and your organisation must be able to justify to the Commissioner (from a reasonable person’s perspective) that the following steps have been considered and/or performed.
1. Understand your obligations in this reform
2. Identify your information held:
![]() Document personal information that flows to and from your entity, including where held in a register (i.e. information stock take)
Document personal information that flows to and from your entity, including where held in a register (i.e. information stock take)
![]() This includes information stored by third party vendors (i.e. Cloud apps, websites, IT contractors, tax agents etc.) and removable disks (i.e. USBs)
This includes information stored by third party vendors (i.e. Cloud apps, websites, IT contractors, tax agents etc.) and removable disks (i.e. USBs)
![]() Identify personal information that is not required to be held and then perform “de-identification” of that personal information so that those individuals may no longer be identified.
Identify personal information that is not required to be held and then perform “de-identification” of that personal information so that those individuals may no longer be identified.
3. Risk assessment and protection
![]() Identify potential risks and vulnerabilities (i.e. unauthorised access, interference, loss and misuse)
Identify potential risks and vulnerabilities (i.e. unauthorised access, interference, loss and misuse)
![]() Implement controls for each risk (i.e. policies, process changes, systems upgrades, change contractors etc.)
Implement controls for each risk (i.e. policies, process changes, systems upgrades, change contractors etc.)
![]() Identify how and when you will be notified of a breach
Identify how and when you will be notified of a breach
4. Document and implement a Breach Response and Reporting Plan
5. Start engaging with external reporting channels (OAIC, security contractors etc.) That way if a breach occurs you will have a known access point.
6. Adequate data breach insurance
7. Consult a suitable advisors
8. Maintain ongoing discussions and training at staff, executive and board level.
Prevention is better than cure
The OAIC does not require organisations to be “data breach proof”. Rather, the purpose of the scheme is to foster proactive remedial actions so that when a breach does occur, the likelihood of serious harm to the affected individuals is minimised.
If the organisation takes remedial actions that prevent the likelihood of serious harm occurring for any individuals whose personal information is involved in the data breach, then the breach is not considered an eligible data breach.
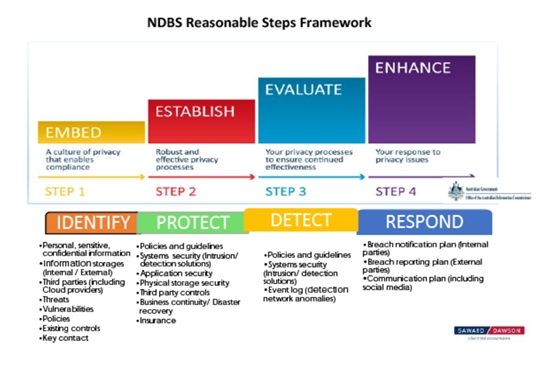
We encourage all our clients to implement the privacy management steps described in the previous section. They are laid out within our privacy management program which follows a methodical process and can be bolted onto your existing governance, risk management, systems governance, and internal control processes.
Do you need help?
We have been assisting our clients to assess existing privacy compliance processes, including designing privacy management programs. Our Privacy Management Program helps you to see the “big picture” without getting held up in unnecessary details.
Please contact us and see how we can assist your organisation’s risk assessments, regulatory compliance and reporting mechanisms. Remember, you need to be able to demonstrate to the Commissioner that the steps listed above have been considered and/or performed.



